Stealth Alternate Data Streams and Other ADS Weirdness
Matt • September 20, 2011
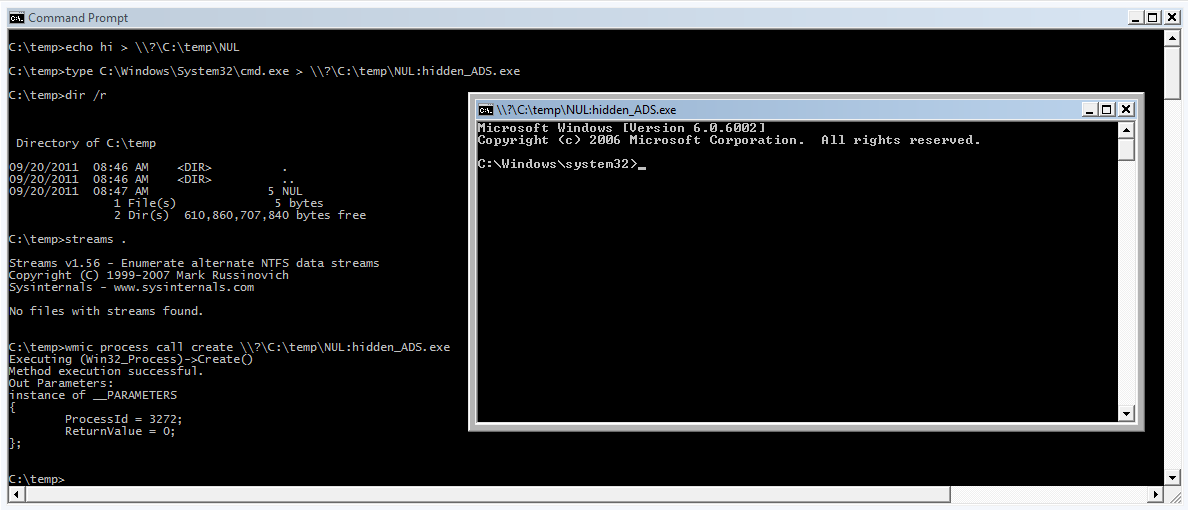
C:\temp>echo hi > \\?\C:\temp\NUL
C:\temp>type C:\Windows\System32\cmd.exe > \\?\C:\temp\NUL:hidden_ADS.exe
C:\temp>dir /r C:\temp
Directory of C:\temp
09/17/2011 06:35 AM <DIR> .
09/17/2011 06:35 AM <DIR> ..
09/17/2011 06:37 AM 5 NUL
1 File(s) 5 bytes
C:\temp>streams C:\temp
Streams v1.56 - Enumerate alternate NTFS data streams
Copyright (C) 1999-2007 Mark Russinovich
Sysinternals - www.sysinternals.com
No files with streams found.
C:\temp>wmic process call create \\?\C:\temp\NUL:hidden_ADS.exe
Executing (Win32_Process)->Create()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ProcessId = 1620;
ReturnValue = 0;
};
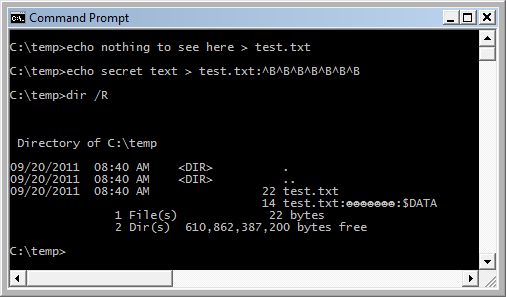
C:\temp>echo hi > C:\temp\test.txt
C:\temp>echo secret text > C:\temp\test.txt:^G^G^G
C:\temp>dir /R C:\temp
Directory of C:\temp
09/17/2011 07:09 AM <DIR> .
09/17/2011 07:09 AM <DIR> ..
09/17/2011 07:08 AM 5 test.txt
14 test.txt::$DATA
1 File(s) 5 bytes
C:\temp>more < C:\temp\test.txt:^G^G^G
secret text

Recently, I had the privilege to write a detailed analysis of CVE-2023-34362, which is series of several vulnerabilities in the MOVEit file transfer application that lead to remote code execution. One of the several vulnerabilities involved an ISAPI module - specifically, the MoveITISAPI.dll ISAPI extension. One of the many vulnerabilities that comprised the MOVEit RCE was a header-injection issue, where the ISAPI application parsed headers differently than the .net application. This point is going to dig into how to analyze and reverse engineer an ISAPI-based service! This wasn’t the first time in the recent past I’d had to work on something written as an ISAPI module, and each time I feel like I have to start over and remember how it’s supposed to work. This time, I thought I’d combine my hastily-scrawled notes with some Googling, and try to write something that I (and others) can use in the future. As such, this will be a quick intro to ISAPI applications from the angle that matters to me - how to reverse engineer and debug them! I want to preface this with: I’m not a Windows developer, and I’ve never run an IIS server on purpose. That means that I am approaching this with brute-force ignorance! I don’t have a lot of background context nor do I know the correct terminology for a lot of this stuff. Instead, I’m going to treat these are typical DLLs from typical applications, and approach them as such.