MITRE ATT&CK Tactics Are Not Tactics
Richard Bejtlich • October 23, 2020
Introduction
At a high-level, ATT&CK is a behavioral model that consists of the following core components:
• Tactics, denoting short-term, tactical adversary goals during an attack;
• Techniques, describing the means by which adversaries achieve tactical goals;
• Sub-techniques, describing more specific means by which adversaries achieve tactical goals at a lower level than techniques; and
• Documented adversary usage of techniques, their procedures, and other metadata.
My concern is with MITRE's definition of "tactics" as "short-term, tactical adversary goals during an attack," which is oddly recursive.
The key word in the tactics definition is goals
. According to MITRE, "tactics" are "goals."
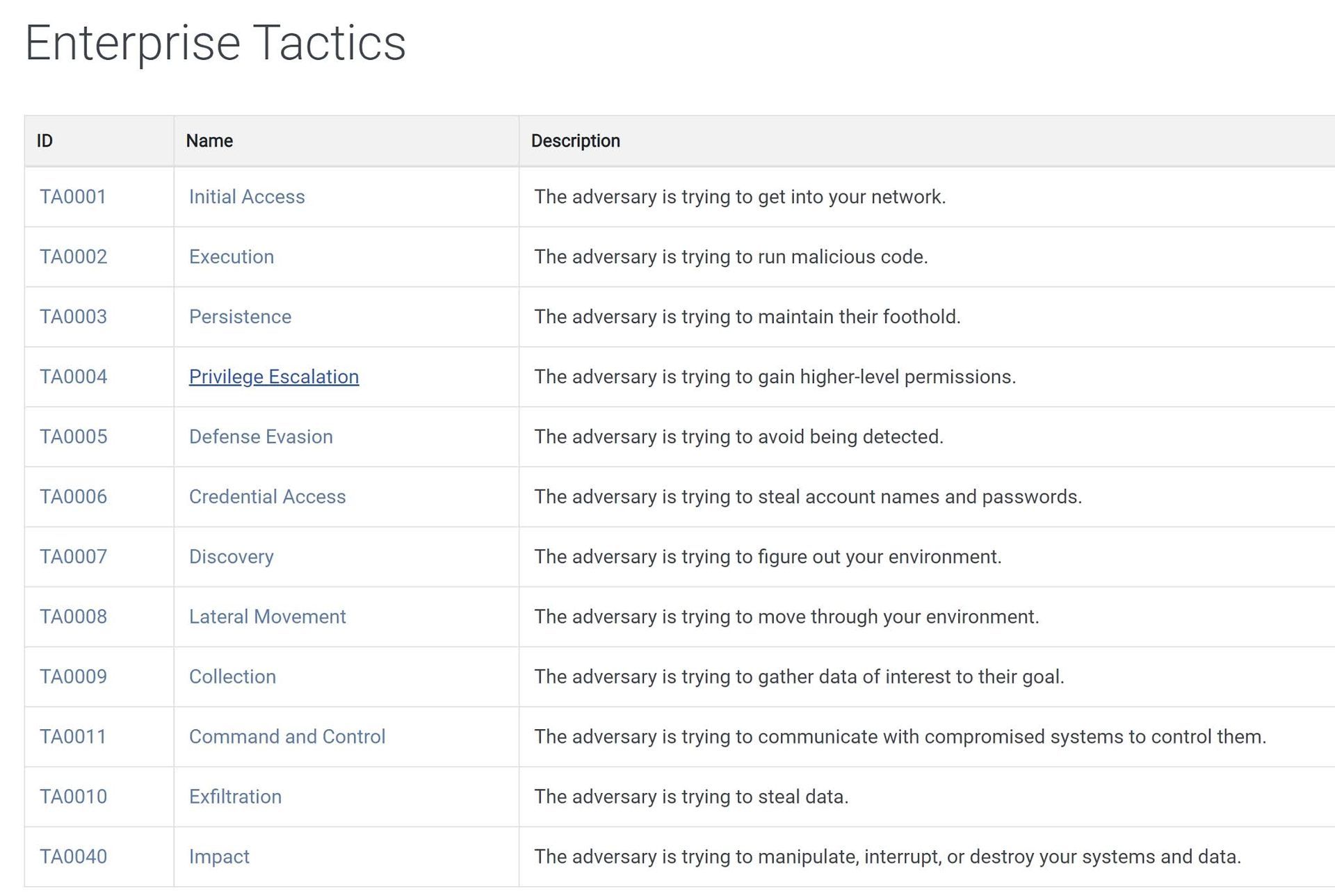
Examples of ATT&CK Tactics
ATT&CK lists the following as " Enterprise Tactics
":
goals
Military Theory and Definitions
employment and ordered arrangement of forces in relation to each other.
On Tactics
use
"Tactics, in warfare, the art and science of fighting battles on land, on sea, and in the air. It is concerned with the approach to combat; the disposition of troops and other personalities; the use made of various arms, ships, or aircraft; and the execution of movements for attack or defense...
The word tactics originates in the Greek taxis
, meaning order, arrangement, or disposition -- including the kind of disposition in which armed formations used to enter and fight battles.
From this, the Greek historian Xenophon derived the term tactica
, the art of drawing up soldiers in array. Likewise, the Tactica
, an early 10th-century handbook said to have been written under the supervision of the Byzantine emperor Leo VI the Wise, dealt with formations as well as weapons and the ways of fighting
with them.
The term tactics fell into disuse during the European Middle Ages. It reappeared only toward the end of the 17th century, when “Tacticks” was used by the English encyclopaedist John Harris to mean 'the Art of Disposing
any Number of Men into a proposed form of Battle...'"
From these three examples, it is clear that tactics are about use and disposition of forces or capabilities during engagements. Goals are entirely different. Tactics are the methods by which leaders achieve goals.
How Did This Happen?
I was not a fly on the wall when the MITRE team designed ATT&CK. Perhaps the MITRE team fixated on the phrase"tactics, techniques, and procedures," or "TTPs," again derived from military examples, when they were designing ATT&CK? TTPs became hot during the 2000s as incident responders drew with military experience drew on that language when developing concepts like indicators of compromise. That fixation might have led MITRE to use "tactics" for their top-level structure.
It would have made more sense for MITRE to have just said "goal" or "objective," but "GTP" isn't recognized by the digital defender world.
It's Not Just the Military
Some readers might think "ATT&CK isn't a military tool, so your military examples don't apply." I use the military references to show that the word tactic does have military origins, like the word "strategy," from the Greek Strategos
or strategus
, plural strategoi
, (Greek: στρατηγός, pl. στρατηγοί; Doric Greek: στραταγός, stratagos
; meaning "army leader").
That said, I would be surprised to see the word tactics used as "goals" anywhere else. For example, none of these examples from the non-military world involve tactics as goals:
This Harvard Business Review article
defines tactics as "the day-to-day and month-to-month decisions required to manage a business."
Conclusion
common language
Update

Recently, I had the privilege to write a detailed analysis of CVE-2023-34362, which is series of several vulnerabilities in the MOVEit file transfer application that lead to remote code execution. One of the several vulnerabilities involved an ISAPI module - specifically, the MoveITISAPI.dll ISAPI extension. One of the many vulnerabilities that comprised the MOVEit RCE was a header-injection issue, where the ISAPI application parsed headers differently than the .net application. This point is going to dig into how to analyze and reverse engineer an ISAPI-based service! This wasn’t the first time in the recent past I’d had to work on something written as an ISAPI module, and each time I feel like I have to start over and remember how it’s supposed to work. This time, I thought I’d combine my hastily-scrawled notes with some Googling, and try to write something that I (and others) can use in the future. As such, this will be a quick intro to ISAPI applications from the angle that matters to me - how to reverse engineer and debug them! I want to preface this with: I’m not a Windows developer, and I’ve never run an IIS server on purpose. That means that I am approaching this with brute-force ignorance! I don’t have a lot of background context nor do I know the correct terminology for a lot of this stuff. Instead, I’m going to treat these are typical DLLs from typical applications, and approach them as such.